 Potential Security Vulnerability for Sage X3
Potential Security Vulnerability for Sage X3
Sage takes the security of its customer solutions extremely seriously and regularly releases hotfixes to Sage X3 to resolve potential vulnerabilities. You have likely seen in the news that Sage has released patches for a recent vulnerability that was identified as part of Sage’s ongoing engagement in application security optimization.
The security risk is related to a platform component and has no impact on the Sage X3 application code or customizations that may have been implemented. Should no action be taken, a malicious actor with sufficient knowledge could potentially gain full operating system administrative access to the Sage X3 application server, including access to data and potentially access other parts of the network where the application server is hosted. The risk is higher if the relevant Sage X3 servers are open to the Internet. If the customer’s Sage X3 implementation is not accessible through the Internet, the risk is restricted to individuals with internal network access.
Mitigation
The most immediate action to mitigate is to turn off ADX admin service. Set the AdxAdmin service to “manual” start mode and start the service only when a maintenance operation with the X3 Console is required, then stop the service once the maintenance operation is complete. This will have minimal impact on operations and almost eliminate the potential of damage. Please refer to the ‘Steps to turn off the AdxAdmin service’ section of this document for more information.
Client that run Sage X3 without open access to the public internet will not be impacted. This is the case if you have implemented a network segmentation strategy isolating the administration ports only to authorized personnel such as a VPN or IP-restrictions.
Net at Work will be contacting our Cloud at Work clients to plan and implement remediation. If any of our on premise clients would like assistance, please contact us.
Steps to turn off the ADXADMIN service
Note: This should be done by an experienced IT professional, but does not need to be an X3 professional.
- Remote desktop into the server where the ADXADMIN service is installed.
- Open the Windows Services Manager.
- Locate the Sage Safe X3 AdxAdmin service. Different versions of Sage X3 may use different default names for this service.
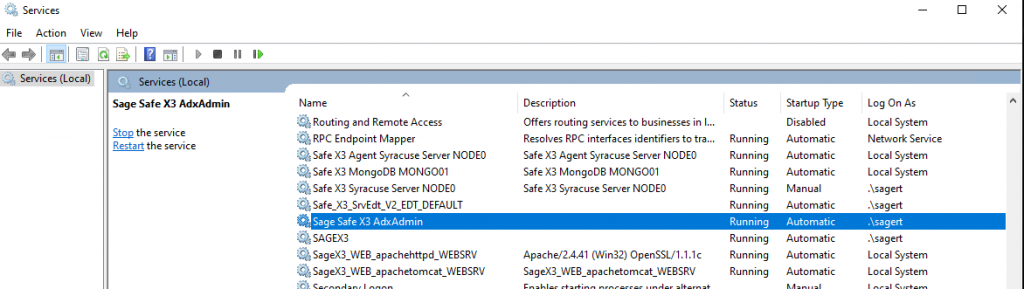
- Double click on the service or right-click and select Properties.
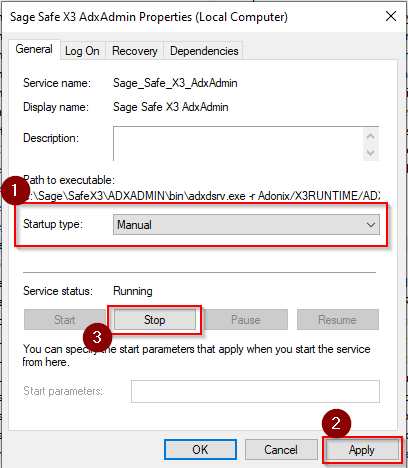
- Edit the Startup Type drop down and select Manual, if not already selected. (1) This will prevent the service from starting automatically when the server restarts.
- Apply the change (2)
- Stop the service if not currently using the Sage X3 Configuration Console (3)
- When the use of the Console is needed again, return to this service and start it. It does not need to be reset to the Automatic startup type.
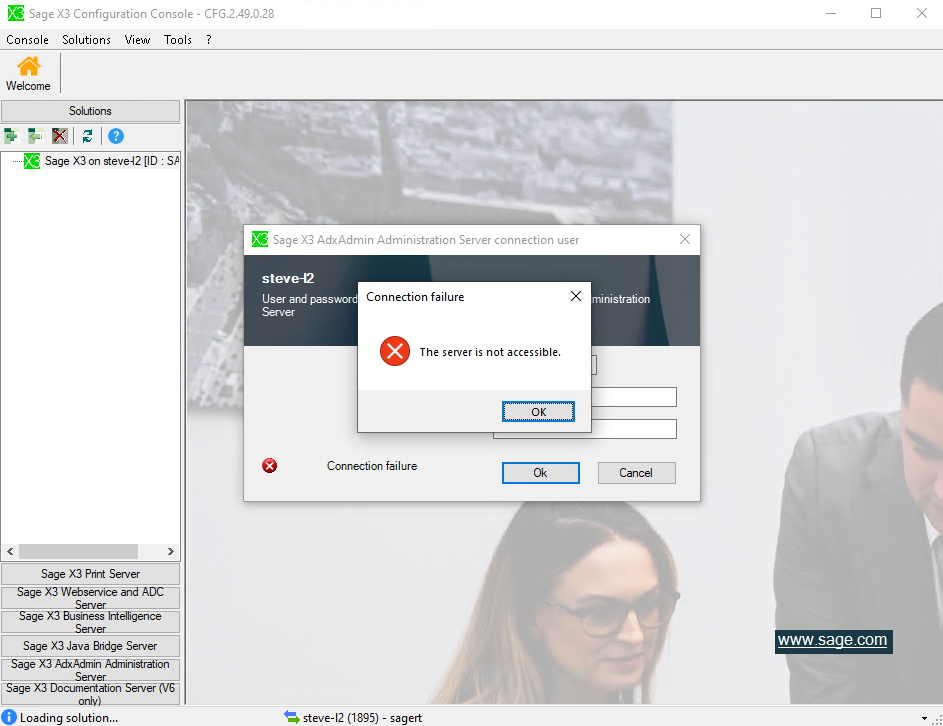
Trying to use the Sage X3 Configuration Console when the ADXADMIN service is turned off will result in an error similar to the below.
For more information about the potential security risk related to the ADXADMNIN service, or any other questions about Sage X3, please contact us.



